1.REFERENCE
. Currently this Policy is being updated to reflect requirements for the California Consumer Privacy Act https://oag.ca.gov/privacy/ccpa and the European Union General Data Protection Regulationshttps://ec.europa.eu/info/law/law-topic/data-protection/data-protection-eu_en . This initial phase is based on compliance with the New York State Information Security Breach and Notification Act of 2005 https://ag.ny.gov/internet/data-breach . If indicated a comprehensive update is targeted for 12/30/20. The intent of www.teetors.org, an “S Corporation” organized in the State of Virginia and physically headquartered at [9 Lenape LN, West Windsor, NJ 08550], is to employ regulatory compliance standards that meet the best practice for supporting its mentees, mentors, and user community
2. OVERVIEW
Misuse, unauthorized disclosure, or compromised Personal and Private Information can pose legal, privacy and security risks; thus, it is important for users to understand the appropriate collection, use, storage, and disposal of Personal and Private Information.
3.DEFINITIONS.
3.1.Personal Information shall mean any information concerning a natural person which, because of name, number, personal mark, or other identifier, can be used to identify such natural person.
3.2.Internal Information. To include contact lists, correspondence, meeting minutes, procedural documentation, and trade secrets.
3.3.Confidential Information. To include educational information, employment information, legally privileged information, or subject to a confidentiality agreement.
3.4.Private Information. shall mean personal information consisting of any information in combination with any one or more of the following data elements, when either the personal information or the data element is not encrypted, or encrypted with an encryption key that has also been acquired:
3.4.1. social security number.
3.4.2. driver's license number or non-driver identification card number; or
3.4.3. account number, credit, or debit card number, in combination with any required security code, access code, or password that would permit access to an individual's financial account.
3.4.4. criminal background data, electronic credentials, medical information, and information of individuals under 13 years of age.
3.4.5. "Private information" does not include publicly available information which is lawfully made available to the public from federal, state, or local government records.
4. PURPOSE
The purpose of this Data Protection Policy is to ensure the proper use of any Personal and Private Information that www.teetors.org might collect(s) and retain(s); and make users aware of what www.teetors.org deems as acceptable and unacceptable classification, collection, access, use, storage, retention, and disposal of such information
5.SCOPE
This policy covers appropriate classification, collection, and usage of information and applies to all employees, vendors, and agents operating on behalf of www.teetors.org.
6. POLICY
6.1.Classification
6.1.1. Public. Public data is information that may be disclosed to any person regardless of affiliation with the company. Examples of Public data include company contact information, service offerings, and company certifications and affiliations.
6.1.2. Internal Internal data is information that is potentially sensitive and is not intended to be shared with the public. Examples of Internal data include correspondence, meeting minutes, contact lists that contain information that is not publicly available, and procedural documentation that should remain internal.
6.1.3. Confidential Confidential data is information that if made available to unauthorized parties, may adversely affect individuals or the company. This may include data that is required to be keep confidential, either by law or under a confidentiality agreement with a third party. This information should be protected against unauthorized disclosure or modification. Confidential data should be used only when necessary for business purposes and should be protected both when it is in use and when it is being stored or transported. Examples of Confidential data include legally privileged information, information subject to a confidentiality agreement, and personal information that is not otherwise publicly available.
6.1.4. Restricted Use. Restricted Use data includes any information that the company has a contractual, legal, or regulatory obligation to safeguard in the most stringent manner. In certain cases, unauthorized disclosure or loss of this data would require the company to notify the affected individual and state or federal authorities. Restricted Use data should be used only as necessary and carefully protected. It should be encrypted both in transit and when stored. Examples of Restricted Use data include private information, criminal background data, electronic credentials used to authenticate individuals, protected health information, and financial account numbers.
6.2. Labeling
6.2.1. Review what is currently stored for accuracy, relevancy, and completeness.
6.2.2. ‘Chief Information Officer’ will develop schedule to appropriately label information in accordance with 6.1 Classification.
6.3 .Retention
6.3.1. Review what is currently stored for accuracy, relevancy, and completeness.
6.3.2. ‘Chief Information Officer’ will develop schedule for periodic review of Personal and Private Information.
6.3.3. Personal Information will be maintained for 10 years after individual leaves company.
6.3.4. Private Information will be maintained for 5 months after individual leaves company.
6.3.5. Public information will be maintained for 60 months.
6.3.6. Internal information will be maintained for 10 years.
6.3.7. Confidential information will be maintained for 10 years.
6.3.8. Restricted Use information will be maintained for 10 years.
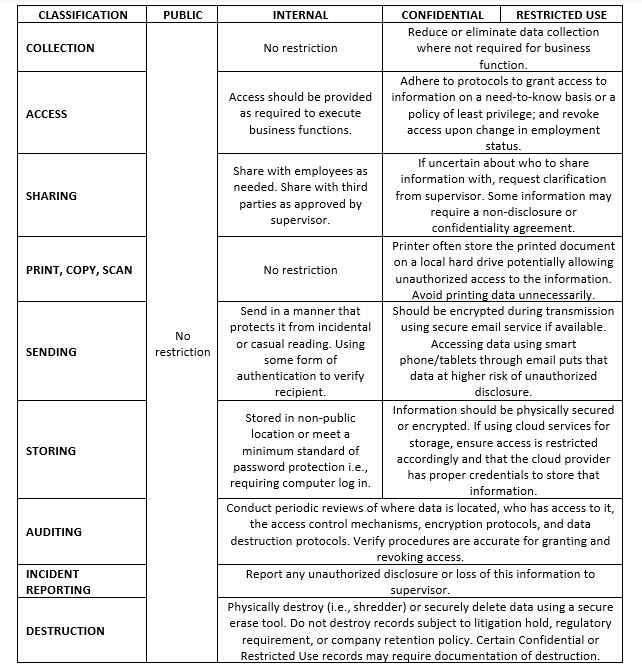
6.4. The below table identifies the appropriate method of collection, access, sharing, reproduction, sending, storing, auditing, incident reporting, and destruction for various classifications of data.
7. POLICY COMPLIANCE.
7.1.Compliance MeasurementThe management team will verify compliance to this policy through various methods, including but not limited to, periodic walk-through, video monitoring, business tool reports, internal and external audits, and feedback to the policy owner.
7.2. ExceptionsAny exception to the policy must be approved by the management team in writing and in advance.
7.3. Non-Compliance. An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.
Table of content
Password Construction & Protection Policy
1. OVERVIEW.
Passwords are a critical component of information security. Passwords serve to protect user accounts; however, a poorly constructed password may result in the compromise of individual systems, data, or the company’s network. This guideline provides best practices for creating secure passwords. All users, including contractors and vendors with access to TeeTors.org systems, are responsible for taking the appropriate steps, as outlined below, to select and secure their passwords.
2. PURPOSE.
The purpose of this policy is to establish standards and best practices for creating strong passwords, the protection of those passwords, and the frequency of change.
3.SCOPE.
This guideline applies to employees, contractors, consultants, temporary and other workers at TeeTors.org, including all personnel affiliated with third parties. This guideline applies to all passwords including but not limited to user-level accounts, system-level accounts, web accounts, e-mail accounts, screen saver protection, voicemail, and local router logins.
3.2.Internal Information. To include contact lists, correspondence, meeting minutes, procedural documentation, and trade secrets.
4. POLICY
All passwords should meet or exceed the following guidelines
4.1. Password Creation.
4.1.1. All user-level and system-level passwords must conform to 4.2 Password Construction Guidelines.
4.1.2. Users must not use the same password for TeeTors.org accounts as for other non- TeeTors.org access (for example, personal ISP account, option trading, benefits, and so on)
4.1.3. Where possible, users must not use the same password for various TeeTors.org access needs.
4.1.4. User accounts that have system-level privileges, granted through group memberships or programs, must have a unique password from all other accounts held by that user to access system-level privileges.
4.1.5. Where Simple Network Management Protocol (SNMP) is used, the community strings must be defined as something other than the standard defaults of public, private, and system and must be different from the passwords used to log in interactively. SNMP community strings must meet password construction guidelines.
4.2. Password Construction Guidelines. Strong passwords have the following characteristics:
4.2.1. Contain at least eight alphanumeric characters.
4.2.2. Contain both upper- and lower-case letters.
4.2.3. Contain at least one number (for example, 0-9).
4.2.4. Contain at least one special character (for example,$%^&*()_+|~-=\`{}[]:";'<>?,/).
4.3. Improper Password Construction Poor, or weak, passwords have the following characteristics:
4.3.1. Contain less than eight characters.
4.3.2. Can be found in a dictionary, including foreign language, or exist in a language slang, dialect, or jargon.
4.3.3. Contain personal information such as birthdates, addresses, phone numbers, or names of family members, pets, friends, and fantasy characters.
4.3.4. Contain work-related information such as building names, system commands, sites, companies, hardware, or software.
4.3.5. Contain number patterns such as aaabbb, qwerty, zyxwvuts, or 123321.
4.3.6. Contain common words spelled backward or preceded or followed by a number (for example, terces, secret1 or 1secret).
4.3.7. Are some version of “Welcome123” “Password123” “Changeme123”
4.4. Password Protection.
4.4.1. Passwords must not be shared with anyone. All passwords are to be treated as sensitive, Confidential
4.4.2. Passwords must not be inserted into email messages, Alliance cases or other forms of electronic communication.
4.4.3. Passwords must not be revealed over the phone to anyone.
4.4.4. Do not reveal a password on questionnaires or security forms.
4.4.5. Do not hint at the format of a password (for example, "my family name").
4.4.6. Do not share TeeTors.org passwords with anyone, including administrative assistants, secretaries, managers, co-workers while on vacation, and family members.
4.4.7. Do not write passwords down and store them anywhere in your office. Do not store passwords in a file on a computer system or mobile devices (phone, tablet) without encryption.
4.4.8. Do not use the "Remember Password" feature of applications (for example, web browsers).
4.4.9. Any user suspecting that his/her password may have been compromised must report the incident and change all passwords.
Use of Password and Passphrases.
4.4.10. Passphrases are generally used for public/private key authentication. A public/private key system defines a mathematical relationship between the public key that is known by all, and the private key, that is known only to the user. Without the passphrase to "unlock" the private key, the user cannot gain access.
4.4.11. Passphrases are not the same as passwords. A passphrase is a longer version of a password and is, therefore, more secure. A passphrase is typically composed of multiple words. Because of this, a passphrase is more secure against "dictionary attacks."
4.4.12. A good passphrase is relatively long and contains a combination of upper and lowercase letters and numeric and punctuation characters. An example of a good passphrase is based on a song title, affirmation, or other phrase. For example, the phrase, "This May Be One Way To Remember" could become the password TmB1w2R! or another variation. (NOTE: Do not use either of these examples as passwords!)
4.4.13. All the rules above that apply to passwords apply to passphrases.
5. POLICY COMPLIANCE.
5.1. Compliance Measurement. The management team will verify compliance to this policy through various methods, including but not limited to, periodic walk-through, video monitoring, business tool reports, internal and external audits, and feedback to the policy owner.
5.2. ExceptionsAny exception to the policy must be approved by the management team in writing and in advance
5.3. Non-ComplianceAn employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.